Spyderbat Guardian
Application drift refers to when the system state at runtime deviates from the intended or expected state. Drift occurs from a variety of reasons; software updates, ad hoc system changes, misconfigurations, etc. Even as we manage configuration through policy-as-code, drift is inevitable due to the complexity of modern application development environments. Composed of hundreds, sometimes thousands, of discrete components, continuous updates lead to unintended drift and errors, causing downtime and security risk. The only sure-fire way to protect against drift is to monitor for it at runtime.
Say goodbye to application interruptions and hello to sustained uptime.
Spyderbat Guardian automatically protects known-good application behavior to eliminate drift and correct anomalies early in the development process.
Auto-generate the right guardrails
Short-circuit policy creation by capturing your actual observed workload behaviors.
- Remove the guesswork and tuning required by ‘out-of-box’ application control policies that do not understand your application behaviors.
- Spyderbat suggests policies from how your application behaves at runtime.
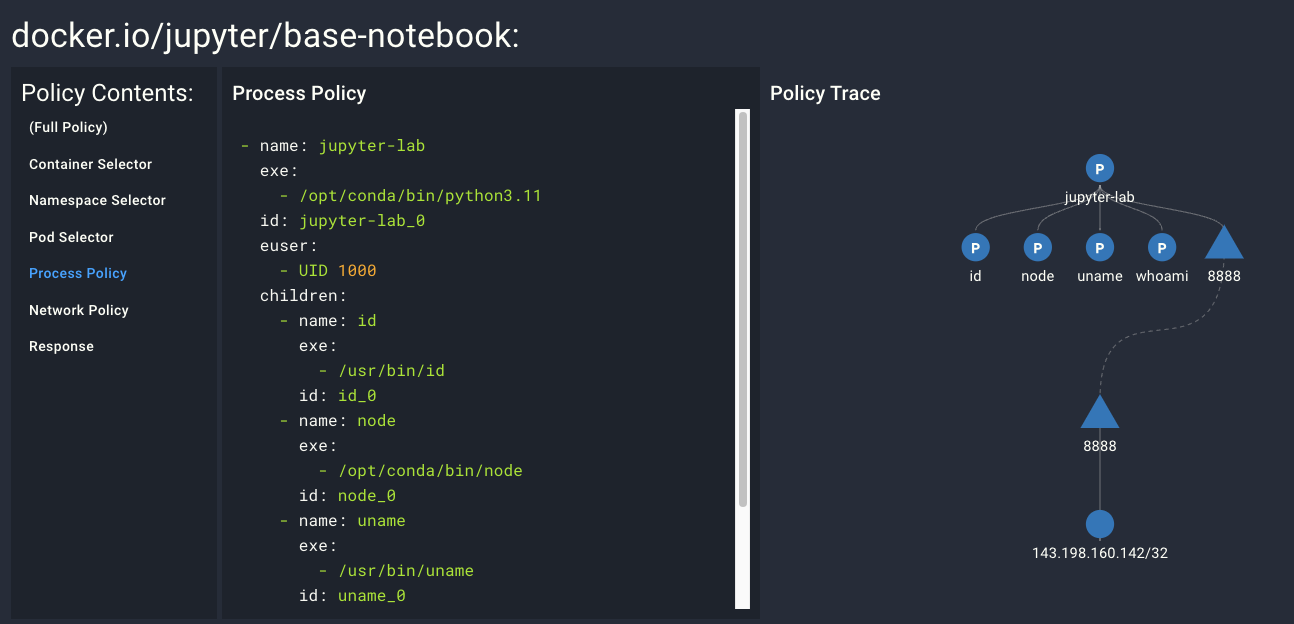
Integrate to your GitOps culture
Programmatically validate workload behaviors throughout the development process.
- Enable developers to confirm their code’s runtime execution behavior aligned to their build processes.
- Whether through CLI, UI, or API, weave Spyderbat into the development culture and catch misconfigurations, supply chain compromise, and insider threats way before they risk production downtime.
Stop Digging. More Building.
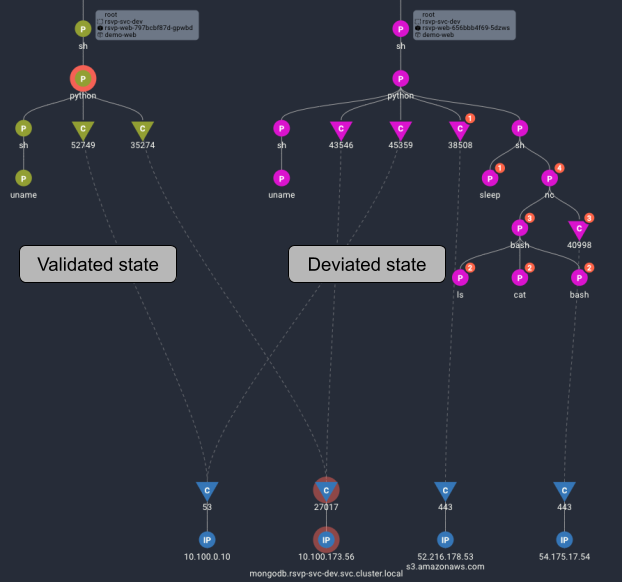
Detects drift from intended states as it occurs.
- Eliminate wasted cycles digging through logs to figure out ‘what happened’.
- Inspect ‘validated’ and ‘deviated’ states (via UI or YAML) for immediate root cause analysis and fast remediation.
Automate policy violation response
Take the right action based on where it occurs.
Nuance policy responses based on namespace, pod, or even the Linux process.
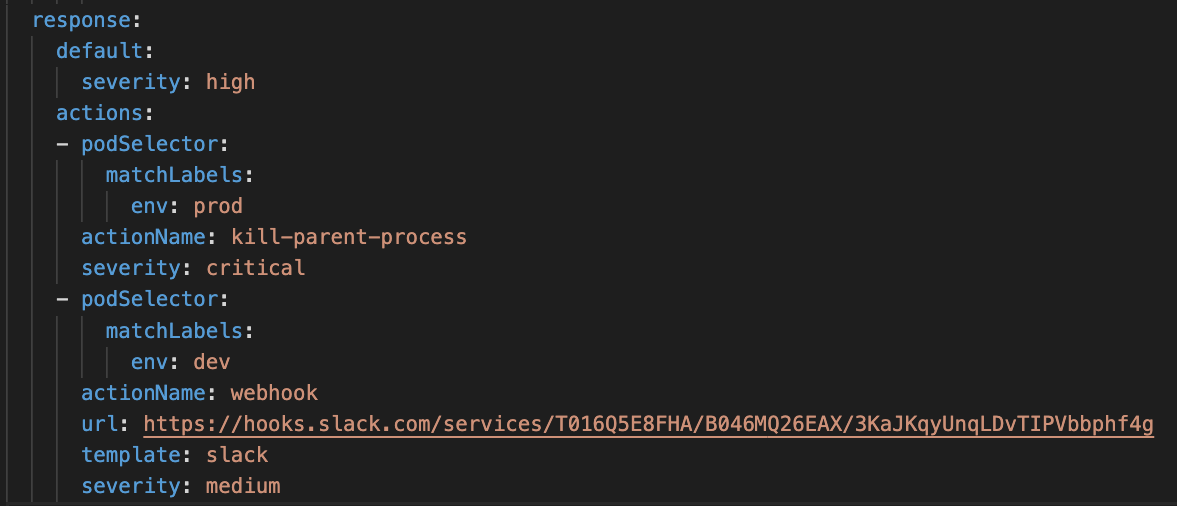
For example, the YAML policy in the screenshot:
- Flags all policy violations with a high severity.
- Sends a slack message to software engineers for violations captured in “dev” pods.
- Kills the process tree for violations captured in “prod” pods.