How leveraging eBPF for Kubernetes and cloud runtime security provides true discovery, superior IDS/IPS, instant root cause, and workload protection while using less than two percent of cloud resources (10x less) for AWS, Azure, GCP and more.

eBPF for Cloud Security and Visibility
eBPF provides a new level of observability and control for applications, by essentially extending access to the what the operating system is doing, or can do, at runtime. The potential uses for eBPF are well and truly staggering, so for the purposes of this quick overview, we'll focus on some of the networking and runtime process-related aspects of eBPF.
Modern applications are, by design, abstracted from their host hardware and related operating systems. App code is typically containerized, separated by microservices, and deployed across clusters of servers. This level of abstraction has many benefits for scale, software development, and more, but observing the system as a whole becomes a patchwork process of collecting and matching network operations data from individual servers and containers – the latter of which generally do not log or persist network data. By enabling kernel-level programs, eBPF elegantly solves this problem by capturing network operations on servers and containers in real-time.
eBPF and AuditD
For Linux users, talk of a kernel-level tool with implications for incident investigation likely sounds reminiscent of Linux’s native activity capturing feature, AuditD. eBPF and AuditD do share some common capabilities such as monitoring for system calls, file access, and other configurable events. Nevertheless, AuditD falls far short of eBPF for system-level visibility into modern cloud and multi-cloud environments. In particular, AuditD:
- Creates excessive userspace syscall overhead
- Often shows invocations such as execveat without revealing what they were called on
- Is inherently container-unaware
In contrast, eBPF is built into the Linux Kernel and container-aware.
Transforming eBPF into Actionable Insights with Spyderbat
Spyderbat offers an industry-first eBPF-based security solution for cloud native runtime environments. Using a lightweight nano agent that probes eBPF, Spyderbat captures real-time stateful observability within and across hosts and containers, without needing to collect and process data from other disparate log sources.
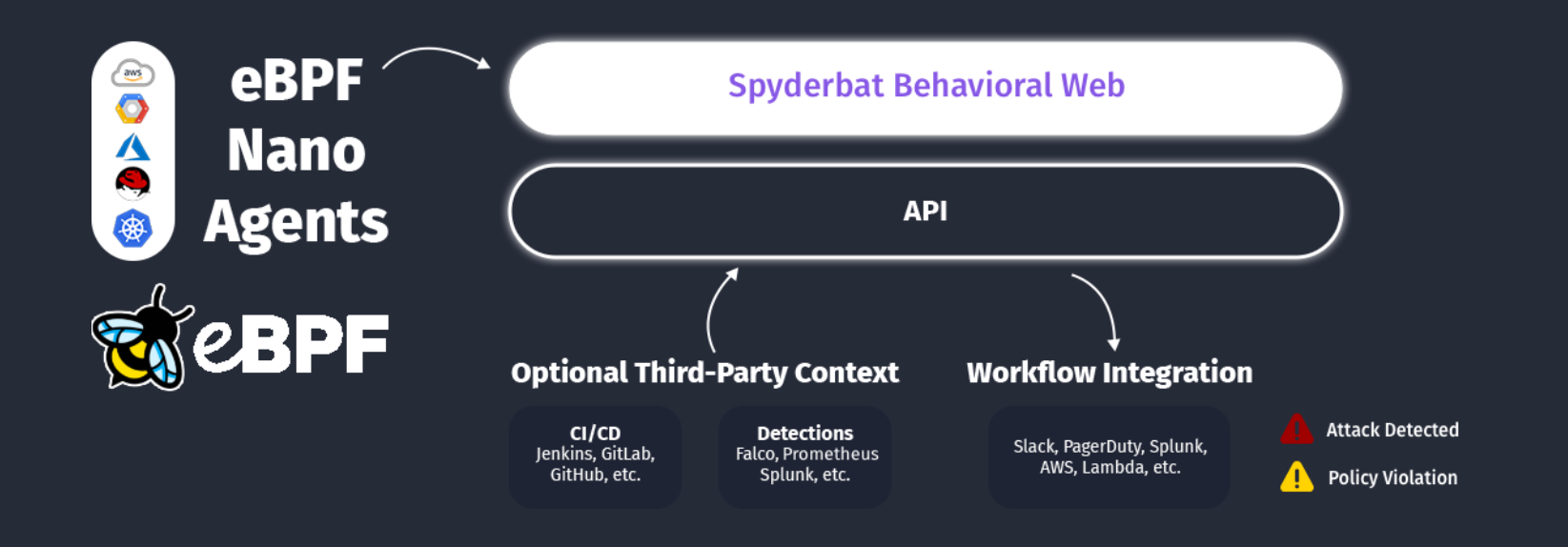
(Spyderbat architecture - container and cloud runtime security with eBPF)
With Spyderbat, engineers don’t have to spend countless hours manually reconstructing event narratives after the fact from incomplete records. Instead, Spyderbat automaticaly stitches together causal sequences of activities as they occur from eBPF data. This includes connecting incoming/outgoing network connections from hosts and containers to their respective processes. Spyderbat both visualizes these causal sequences of activities as Spydertrace, as well as assesses a risk score for every Spydertrace with new activities.
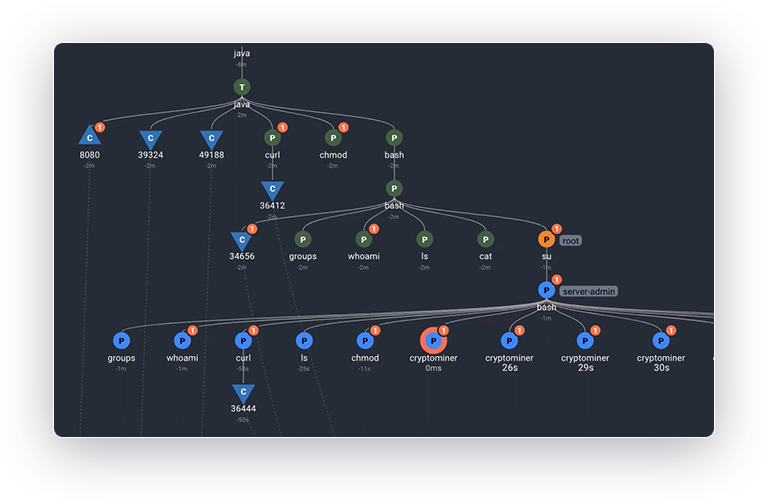
Platform and Security teams use Spyderbat to observe activities live and in granular causal context, enabling automated root cause identification, early problem recognition, and attack detection.
The Next Generation Runtime Security Built for Kubernetes and Multi-Cloud
As the next generation runtime security, Spyderbat provides true IDS/IPS, posture management, and remediation in runtime for Kubernetes and multi-cloud. See how you can:
- Gain complete visibility and control in all regions by harnessing the power of eBPF Spyderbat eBPF Nano Agents.
- Collect kernel-level workload data with negligible performance impact and no management overhead (using less than 2% of resources).
- Visualize runtime activity, detect attacks, recognize anomalies, and automatically take the right action to protect app behavior and minimize downtime.
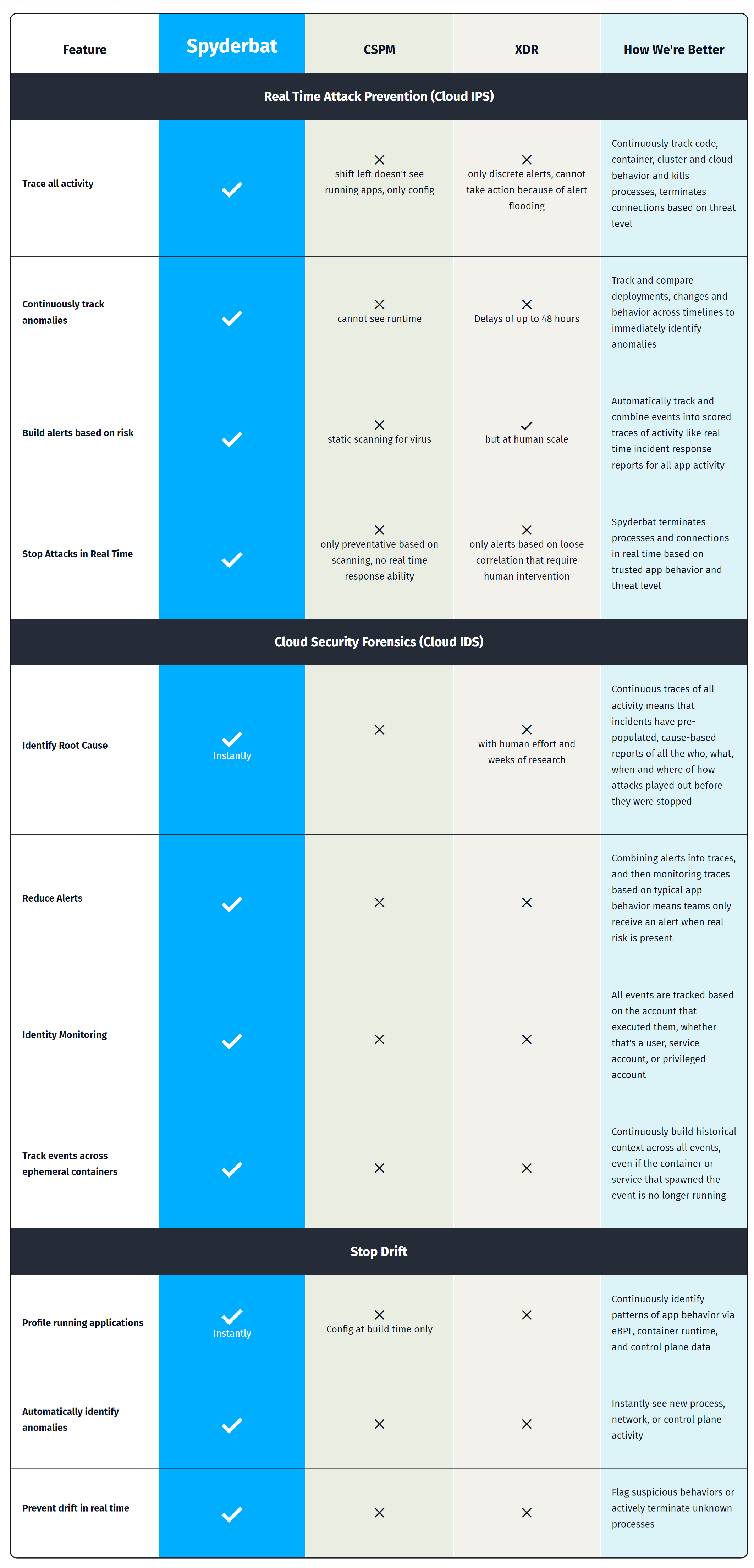
Compare Spyderbat's critical capabilities with other cloud security solutions to see where they fall short. Elevate your cloud runtime security.