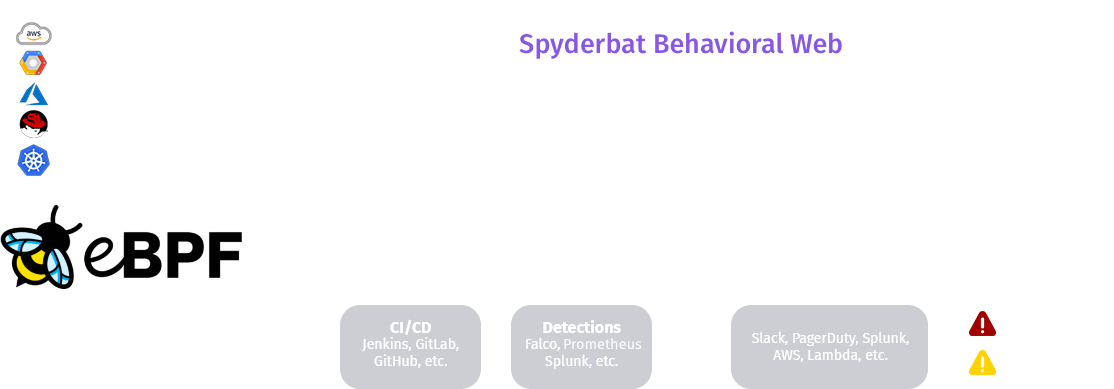
Input API
Spyderbat harnesses the power of eBPF to give you complete visibility and control
Runtime Visibility
Instant root cause of security and operational issues with real time and historical interactive visualizations across Kubernetes, containers and VMs for, with insight to how control plane and data plane runtime behaviors intersect.
Runtime Anomaly Detection
Protect known-good app behavior, and immediately pinpoint deltas to eliminate dwell time and automate action without machine learning black box algorithms. Quickly create policies from actual, observed behavior, rather than endless tuning exercises guessing at your applications runtime policies.
Runtime Intrusion Prevention
Automatically pinpoint and stop rogue processes, connections, or activity that shift-left security can't catch: including supply-chain attacks, compromised credentials, ransomware, and cryptojacking.
Runtime Automated Response
Rollback misconfigurations and stop emerging attacks by taking precise action at the workload. Stop rogue parent processes and restart pods, while alerting the appropriate team(s), using environmental context (e.g. namespaces) to programmatically take the right action.

Harness the power of eBPF
Accuracy, Speed, Completeness
The Spyderbat platform’s architectural components track all runtime system and container activities via eBPF for speed and scale.
Free Whitepaper:
eBPF for Cloud Runtime Security
Learn how eBPF provides a new level of insight and context for cloud operations and security teams.
- Instantly visualize app behavior.
- Reduce alerts and false positives by multiple orders of magnitude.
- Automatically stop risk and block attacks in runtime.